Since Version 2 Traefik supports Kubernetes Ingress and acts as a Kubernetes Ingress controller. This is an alternative to the Traefik specific ingressRoute objects. With v2.2. you can now use plain Kubernetes Ingress Objects together with annotations. Of course you can still use IngressRoute objects if you need them for specific requirements.
I tested this feature within Kubernetes 1.17.3. In this blog post I want to point out the important parts of the configuration. Please note that I provide a details setup for Traefik running within a self managed Kubernetes cluster in my open source project Imixs-Cloud.
The Traefik Deployment Object
In the deployment object for traefik first you need add the ‘kubernetesingress’ provider:
- args:
- --api
....
- --providers.kubernetescrd=true
- --providers.kubernetesingress=true
....This is how my complete deployment configuration looks like.
apiVersion: apps/v1
kind: Deployment
metadata:
labels:
app: traefik
release: traefik
name: traefik
namespace: kube-system
spec:
replicas: 1
selector:
matchLabels:
app: traefik
release: traefik
template:
metadata:
labels:
app: traefik
release: traefik
spec:
containers:
- args:
- --api
- --api.insecure
#- --api.insecure=false
- --api.dashboard=true
- --accesslog
- --global.checknewversion=true
- --entryPoints.traefik.address=:8100
- --entryPoints.web.address=:80
- --entryPoints.websecure.address=:443
# permanent redirecting of all requests on http (80) to https (443)
- --entrypoints.web.http.redirections.entryPoint.to=websecure
- --entrypoints.websecure.http.tls.certResolver=default
# Let's Encrypt Configurtion:
# Please note that this is the staging Let's Encrypt server configuration.
# Once you get things working, you should remove that following line.
- --certificatesresolvers.default.acme.caserver=https://acme-staging-v02.api.letsencrypt.org/dire
- --certificatesresolvers.default.acme.email={YOUR-E-MAIL}
- --certificatesresolvers.default.acme.storage=acme.json
- --certificatesresolvers.default.acme.tlschallenge
- --ping=true
- --providers.kubernetescrd=true
- --providers.kubernetesingress=true
- --log.level=INFO
image: traefik:2.2
imagePullPolicy: IfNotPresent
livenessProbe:
failureThreshold: 3
httpGet:
path: /ping
port: 8100
scheme: HTTP
initialDelaySeconds: 10
periodSeconds: 10
successThreshold: 1
timeoutSeconds: 2
name: traefik
ports:
- containerPort: 8100
name: admin
protocol: TCP
- containerPort: 80
name: web
protocol: TCP
- containerPort: 443
name: websecure
protocol: TCP
readinessProbe:
failureThreshold: 1
httpGet:
path: /ping
port: 8100
scheme: HTTP
initialDelaySeconds: 10
periodSeconds: 10
successThreshold: 1
timeoutSeconds: 2
resources: {}
terminationMessagePath: /dev/termination-log
terminationMessagePolicy: File
dnsPolicy: ClusterFirst
restartPolicy: Always
schedulerName: default-scheduler
securityContext: {}
serviceAccount: traefik
serviceAccountName: traefik
terminationGracePeriodSeconds: 60
Permanent HTTP->HTTPS Redirect
In the example configuration above I have configured a permanent redirect from HTTP to HTTPS. So you do not need a extra middleware object.
...
- --entrypoints.web.http.redirections.entryPoint.to=websecure
- --entrypoints.websecure.http.tls.certResolver=default
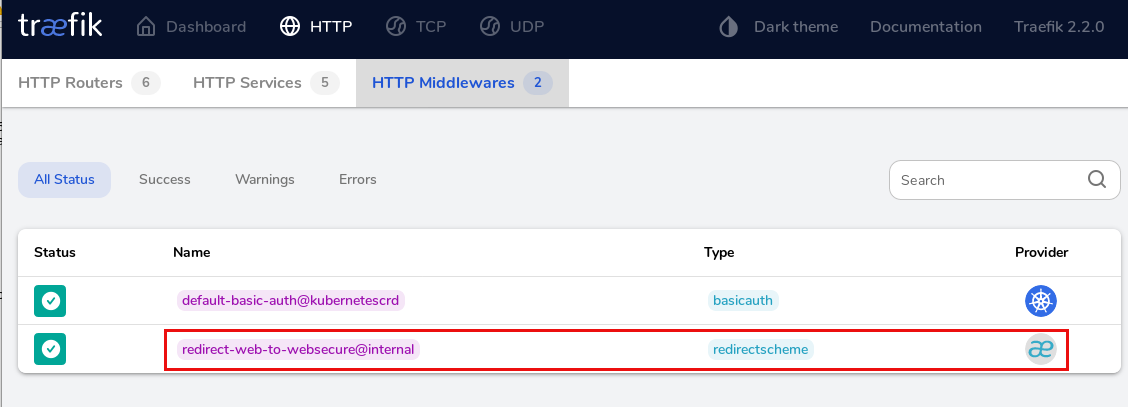
....The Redirect scheme can be controlled from the Traefik.io web Dashboard in the section Middlewares:
Setup a Ingress Object
Now you can setup the Kubernetes Ingress object using the new annotations provided by Traefik V2.2.:
kind: Ingress
apiVersion: networking.k8s.io/v1beta1
metadata:
name: myingress
annotations:
traefik.ingress.kubernetes.io/router.entrypoints: web, websecure
spec:
rules:
- host: example.foo.com
http:
paths:
- path: /
backend:
serviceName: whoami
servicePort: 80Your new Ingress Network will automatically be redirectef from HTTP to HTTPS due to the Let’s Encrypt configuration. Note, that both entrypoints (web and websecure) are defined in your Ingress.
You will find more information about how to setup Traefik for Kubernetes in the Imixs-Cloud Project site on Github.

Hello Ralph and thanks for your Traefik tutorials.
I wanted to deploy Traefik to my current infra. I have Kibana deployed in the namespace es. I get 404 using the configs below:
—
apiVersion: traefik.containo.us/v1alpha1
kind: Middleware
metadata:
name: basic-auth
namespace: es
spec:
basicAuth:
secret: authsecret
—
apiVersion: v1
kind: Secret
metadata:
name: authsecret
namespace: es
#———— Paste your own password file content here (default user/password=admin/adminadmin)————–
data:
users: |2
YWRtaW46JGFwcjEkWXdmLkF6Um0kc3owTkpQMi55cy56V2svek43aENtLwoKdXNl
cjokYXByMSRaU2VKQW1pOSRVV1AvcDdsQy9KSzdrbXBIMXdGL28uCgo=
—
kind: Ingress
apiVersion: networking.k8s.io/v1beta1
metadata:
name: kibana
namespace: es
annotations:
traefik.ingress.kubernetes.io/router.entrypoints: web, websecure
traefik.ingress.kubernetes.io/router.middlewares: es-basic-auth@kubernetescrd
spec:
rules:
– host: dashboard.guardark.abc
http:
paths:
– path: /
backend:
serviceName: kibana
servicePort: 9192
When I comment this line “traefik.ingress.kubernetes.io/router.middlewares: es-basic-auth@kubernetescrd”, it works.
could you please help?
Regards
If you have 404 this is more a topic to your application (kibana) or with your service configuration and not necessarily of Traefik. You can take a look into the traefik log file. But I guess you will not see a problem there. You can also use the traefik web ui to see if traefik indicates any configuration errors and if traefik is listing you new kibana service.
It may also be helpful if you first try the connection with plan HTTP and do the HTTPS stuff in a second stage. Because the HTTPS topic is tricky.